Courtesy: Analog Devices
Today’s automobiles are becoming increasingly sophisticated, especially with the advancement of self-driving technology. This includes features such as automated steering, acceleration, and braking, as well as convenient options like touchscreen controls and voice commands. Cars are now capable of performing tasks autonomously, such as activating high beams, parking themselves, detecting blind spots, and applying brakes to prevent accidents. These capabilities are made possible by electronic control units (ECUs) that connect to various parts of the vehicle, supporting systems like advanced driver assistance, power management, infotainment, and security. These parts must meet strict manufacturer specifications to ensure safety and performance. However, how does the automotive company ensure these requirements are being met?
One approach is through car part pairing, which involves cryptographic authentication and association between different vehicle subsystems to establish mutual trust. In simpler terms, car part pairing is a unique association of a part with a vehicle. So, trust in automotive components, such as sensors and actuators, requires OEM approval, provability, and secure control throughout their lifecycle.
You may wonder, what are the benefits of car part pairing for the automotive company? Let’s explore a few in this blog.
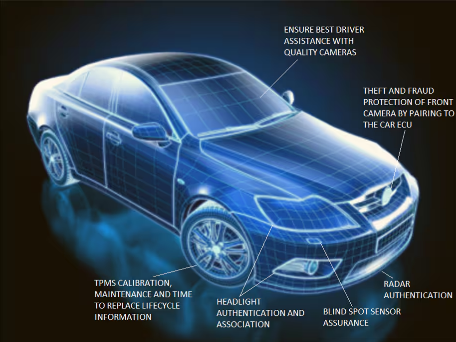
Knowing the Benefits
The primary benefit of pairing is to provide strong cryptographic identification and authentication of car parts. By securely linking specific car parts to specific vehicles, manufacturers can ensure that only authorized parts are used, improving safety and preventing fraud, theft, and counterfeiting. Risks are mitigated through this authentication scheme, as any replacement part must now be authentic and valid, eliminating counterfeit or stolen parts.
Another benefit of pairing is the ability to store and attest to the lifecycle of a car part, including calibration, manufacturing steps, maintenance, mounting, calibration, decommissioning, and relevant traceability information. Cryptographic methods using digital signatures provide formal proof of the car part’s state. This additional information can be used by the car’s ECUs to manage otherwise authentic parts, such as rejecting improperly calibrated OEM ADAS cameras or parts mounted into another car without proper authorization. This attestation of a part’s lifecycle reduces the risk of using invalid parts, even if they are authentic, provided the ECU is secure enough to prevent bypassing part verification.
Ensuring secure lifecycle data is crucial for trust. Tampering with this information could allow refurbishment of worn-out or malfunctioning parts, posing safety risks or using stolen parts. By employing cryptographic-based access control, manufacturers can ensure only authorized parties can modify the car part’s lifecycle information memory and other data used to bind the part to an ECU. Approved OEM dealers can then replace a part, associate it with the car chassis, and perform necessary calibrations.
Applying the Benefits
One of the notable benefits lies in the application of cryptographic methods to establish the authenticity of a car’s installed ADAS camera in relation to the car’s ECU. This is commonly achieved through the utilization of the Elliptic Curve Digital Signature Algorithm (ECDSA) for challenge-response authentication with prior certificate verification.
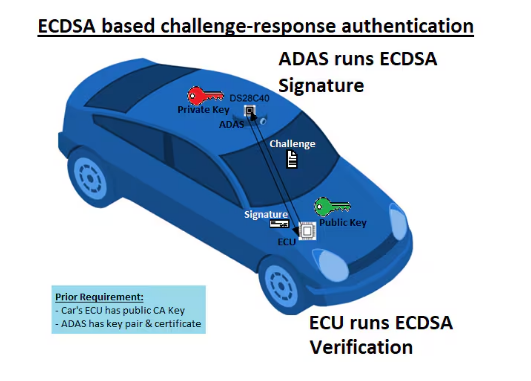
To provide clarity, challenge-response authentication involves the following steps:
- Challenge Initiation:The ECU verifier initiates the process by sending a “challenge” (a randomly generated number) to the ADAS prover.
- Response Generation:The ADAS prover, using a private key, digitally signs the received random number, generating a “response.” Additional information, such as unique identification data, life cycle data and calibration data, may be concatenated with the random number for contextualization.
- Transmission of Response: The ADAS prover then transmits the generated “response” to the ECU.
- Verification Process:The ECU verifier runs a verify, with the public key, using the prover’s identification data and ECDSA signature response to ascertain authenticity. Importantly, this authentication process is bidirectional, capable of being performed in both directions.
This framework ensures robust authentication, affirming the integrity of the ADAS camera’s association (i.e., proving it is paired) with the ECU. Subsequently, cryptographic methods can prove a car’s mounted ADAS camera is paired with proper car’s ECU.
All these benefits listed in this blog can be assured with the DS28C40 Automotive I2C Authenticator IC. Analog Devices offers both the software and experience to implement car part pairing, contributing to building safer automobiles.








