The rapid increase in the rate and severity of cyberattacks is driving an urgent search for dramatically more effective network-security solutions. This post discusses the threat environment facing today’s networks, describes the use of advanced anomaly-detection methods to defend a network from a distributed denial-of-service (D-DoS) attack, and introduces Broadcom’s latest security-enabled switching ASIC, the Trident 4C.
The modern cyber-threat environment
In designing a security solution, a clear understanding of the threat environment, including both the motivation of the attackers and the methods used, is required. Regarding motivation, the objective of a particular network attack typically falls into one of the following, broad categories:
- Reconnaissance: In these attacks, the network is probed for security weaknesses which can be exploited by follow-up attacks;
- Data exfiltration / unauthorized data transfer: In this case, a successful attack can result in the theft of credit card numbers, personal identity information, intellectual property, etc.;
- Denial-of-Service (DoS): The purpose of a DoS attack is to disable or occupy critical network resources, thereby denying service to legitimate users.
It is worth emphasizing a successful attack belonging to any of these categories can result in grave damage, either financial, reputational, or both, to the victim.
On the topic of the mechanics of network intrusion, many points in the network have been attacked and a wide range of methods have been documented. Although the implementation details of any known, prior attack vector are relevant to improving network security, the continuing development by malicious actors of new and more dangerous attacks dictates the need for flexible security solutions capable of responding to known attacks as well as rapid adaptation to emerging threats. Further, the ceaseless growth in network-capacity demand means that a successful security architecture must scale gracefully with bandwidth.
A short description of a distributed, denial-of-service (D-DoS) attack follows to illustrate the nature and scale of security threats faced by today’s networks. Conceptually, a D-DoS attack is: (i) a malicious attempt to disable or occupy network resources; and (ii) an attack with a large “attack surface,” meaning that the malicious traffic making up the attack comes from multiple sources simultaneously. The resources under attack can be physical resources (switches, routers, firewalls, etc.), system resources (network interfaces, servers, computer memory, OS resources, etc.), protocol definitions and implementations, or any combination of the above.
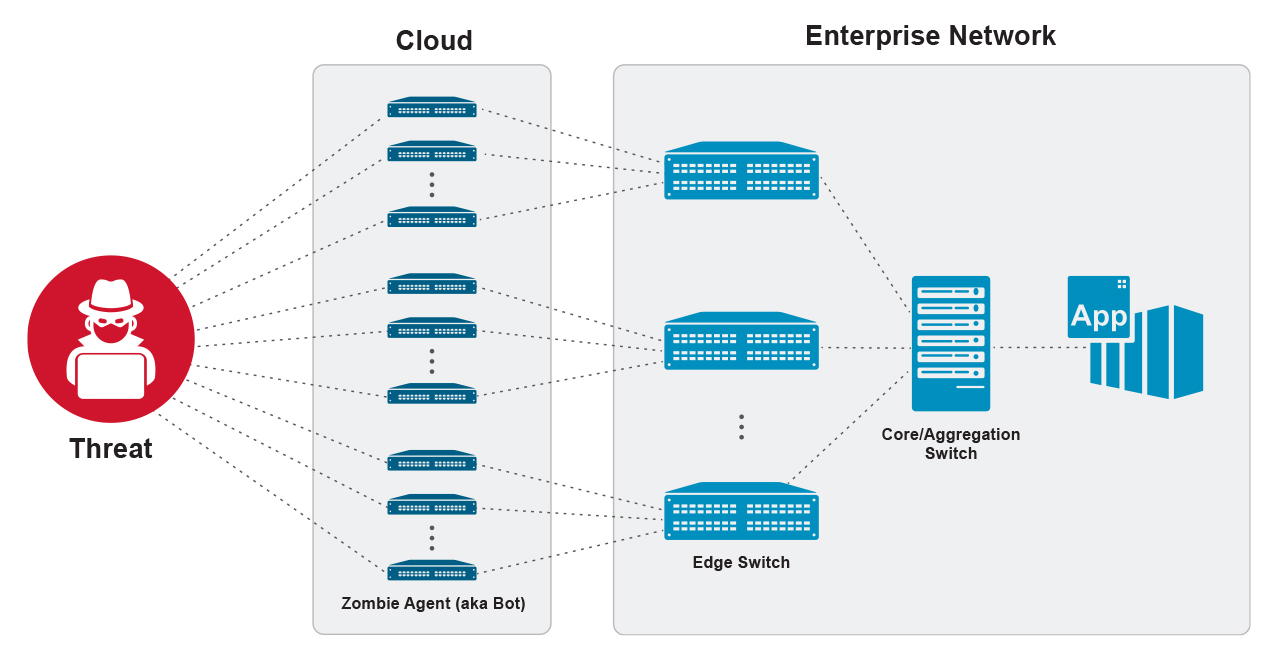
Figure 1 shows the particular case of an attacker attempting to flood the target network with a high volume of junk traffic originating from multiple sources. The attacker has programmed a large constellation of agents (“bots”) to generate malicious traffic addressed to a target application, with the intention of either forcing an error in behavior or simply occupying enough capacity that legitimate users cannot gain access. In most cases, the source address is spoofed, and determining the true origin of the attack is difficult. This category of attack is increasing in frequency, sophistication, and volume of attacking traffic; it has been reported that the total volume of malicious traffic peaked above 1 terabit / second in some recent episodes. Finally, the impact of a D-DoS attack can be quite damaging. For example, the 2016 Mirai attack on Dyn, carried out by a network of hijacked Internet cameras, baby monitors, printers, and other devices took down DNS for large parts of the U.S. for several hours. In this attack, the total number of participating bots was estimated to exceed 1.5 million devices.
Anomaly detection: A key tool in network defense
To detect D-DoS intrusion attempts and other distributed attacks, high-precision measurements of network traffic, together with a detailed analysis of the measurements, are necessary. Today, most network operators rely on traffic probes built into edge switches to provide fine-grained inspection of every packet and packet flow crossing the switch. Although security-enabled edge switches can provide some protection against the D-DoS attack scenario shown in Figure 1, obtaining a comprehensive, end-to-end solution based only on edge-switch security is not possible because each switch sees only a small fraction of the attack surface. Instead, a realization of a robust defense against distributed attacks requires the placement of security functions in the core and aggregation layers, thus providing a network-wide view of the traffic. Implementation of measurement functions in the network interior, however, is challenging due to the high bandwidth and a large number of packet flows.
A common workaround adopted by early attempts to add measurement to the core is to substitute a packet-sampling scheme in place of full-traffic inspection. These implementations, typically capable of inspecting less than one packet in a thousand, suffer from inherent and serious drawbacks due to the fact that for each random packet analyzed, the remaining 99.9% of the traffic passes through unchecked. Although these stop-gap solutions provide some network-wide visibility, they fall far short of what really is needed to deal effectively with distributed attacks, namely a centralized measurement function located in the core and aggregation layers capable of per-packet, per-connection inspection of the entire traffic load.
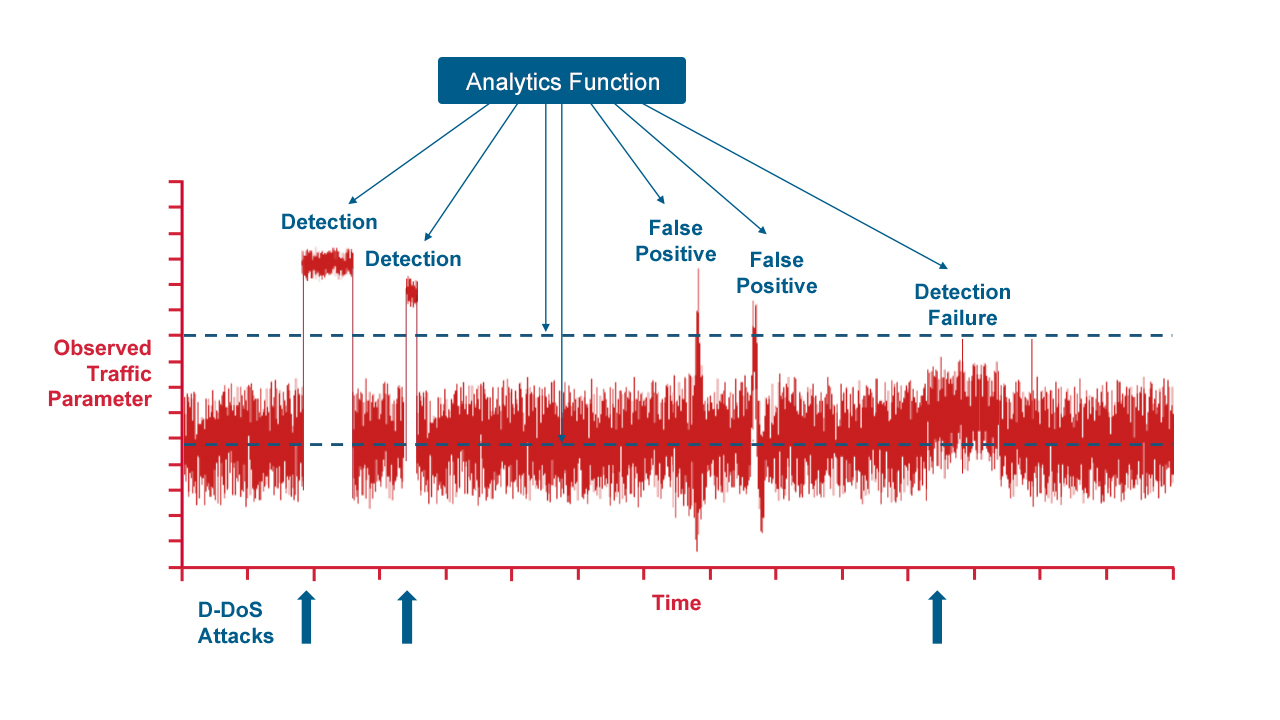
Anomaly detection is the most commonly used strategy for dealing with D-DoS attacks and other intrusion attempts. This method relies on the real-time capture and rendering of time series of selected network-traffic data by the analytics engine, as represented by the red trace in Figure 2. Fine-grained data binning (e.g., 100-millisecond slices) generates the members of the series, and the data can be raw values, such as the bit rate, packet rate, or the number of TCP SYN packets per second, or they can be derived values, such as the entropy of the IP source addresses or the coefficients of a wavelet decomposition. The observed traffic used to construct these series can be the entire traffic load passing through the switch or a chosen subset of the total traffic, such as the traffic on a particular port, a particular subnet, or destined for a particular application. The evolution of the time series is monitored continuously by an analytic function, whose activities are shown in blue in Figure 2. A baseline representing the normal state of the network when free of attack is established, and a threshold is set to serve as a demarcation between ordinary activity and the possible presence of an intrusion attempt. When the data series exhibits an excursion that exceeds the threshold, the analytics function performs peak detection and event discrimination. If the criteria of a particular threat are met, a response is initiated, which often includes the addition of new ACL rules to the switches in the network to drop the attacking traffic. Both statistics-based and AI/ML-based algorithms are used in the implementation of modern analytic systems designed for threat detection.
The problem of false positives is perhaps the biggest challenge for anomaly detection-based surveillance systems. As shown in Figure 2, two episodes of benign activity that briefly cross the detection threshold have been interpreted as intrusion attempts, and any response that suppresses this traffic will harm legitimate users. Also, the analytics function in Figure 2 has failed to detect the relatively low-intensity attack on the far right of the plot. Undetected attacks of this sort typically result in the wasteful utilization or occupation of network resources. In spite of these challenges, however, anomaly detection will be a central component of network security for the foreseeable future. It is the only workable approach capable of providing protection against novel, “Day-Zero” attacks, and improving these systems is a major area of focus in the network security community.
Introducing the Trident 4C
Broadcom’s latest security-capable switch ASIC, the Trident 4C, eliminates the need to compromise between performance and security. This 12.8 Tb/s device supports port speeds from 10 Gb/s to 400 Gb/s, has a fully programmable pipeline, and is suitable for both fixed-configuration and chassis-based designs for the core and aggregation layers. New to this device is a high-performance, high-capacity analytics engine capable of performing per-packet, security monitoring of the entire traffic load. Key features of this industry-leading security solution include:
- Connection-aware monitoring of 500k+ active flows with hardware learning and aging
- 5.4 billion packet inspections /second
- 170 billion ALU operations/second
- 4 million flow-analytic state counters
- Line-rate, programmable security fingerprinting with configurable alarm generation
- Hardware-based record-export module that provides analytical data and alarms to upstream threat-intelligence engines
- 1 million exact-match policy ACLs
Courtesy: Broadcom








