The Internet of Things (IoT) is connecting smart devices and machines to create smart factories (known as Industry 4.0 or Industrial Internet). These highly automated, decentralized factories promise greater efficiency and flexibility across production processes. At the same time they are also exposed to attacks from cyberspace as they rely on Internet connectivity. Software measures alone do not generally provide sufficient protection against these attacks. Hardware-based trust anchors are required to effectively protect smart factories. Infineon’s OPTIGA security controllers provide scalable security for embedded systems, thus protecting machines, data and intellectual property in smart factories.
Smart factories and connected supply chains are presenting many manufacturing companies with new security challenges. Malware, manipulation, sabotage, faulty firmware updates and counterfeit components are examples of advanced threats that can bring entire production lines to a halt and may lead to significant costs and loss of image. The tiniest security gap in a company’s infrastructure can lead to theft of data, intellectual property (IP) and process know-how. Safeguarding this sensitive information calls for tailored solutions that deliver end-to-end protection yet also strike the right balance between security performance requirements and financial constraints. Manufacturers need powerful, reliable and scalable security technologies to safeguard communication between devices and machines within heavily networked infrastructures (figure 1).
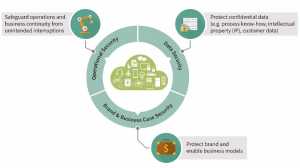
Smart factories and connected supply chains are presenting many manufacturing companies with new security challenges. Malware, manipulation, sabotage, faulty firmware updates and counterfeit components are examples of advanced threats that can bring entire production lines to a halt and may lead to significant costs and loss of image. The tiniest security gap in a company’s infrastructure can lead to theft of data, intellectual property (IP) and process know-how. Safeguarding this sensitive information calls for tailored solutions that deliver end-to-end protection yet also strike the right balance between security performance requirements and financial constraints. Manufacturers need powerful, reliable and scalable security technologies to safeguard communication between devices and machines within heavily networked infrastructures (figure 1).
Secured Identities are the anchor of a security solution for smart factories
In this context, secured identities for machines provide the anchor for implementing any measures to protect electronic exchange and storage of data. As known from daily life where ID cards or passports are used for identification of humans, secured identities are used by machines to reliably identify each other. But even these secured IDs digitally stored on machines could become the subject of attacks and theft.
Hardware-based security solutions based on security chips are the best way to efficiently protect machine identities as well as data and communication. Security controllers provide a greater level of security than concepts that are purely software-based as it is relatively simple to read and overwrite software.
Integrating security chips into all critical nodes helps to prevent unauthorized access to production networks and smart factories.Security chips enable:
- continuous check of component authenticity as well as data and system integrity to prevent manipulation;
- verification of the authenticity of software updates;
- protection of remote access activities;
- robust protection against low-quality, counterfeit spare parts and repair tools.
Chip solutions also provide cryptographic functionality such as public key cryptography and key management. Although these functions could be implemented in both software and hardware, for industrial applications, a hardware-based solution such as a dedicated security chip has clear benefits and can add real value for manufacturers.
Silicon manufacturers such as Infineon Technologies use highly secured, certified processes to personalize hardware trust anchors, i.e. providing a secured identity to each security chip. This often includes a set of keys and certificates stored on the chip in order to allow other devices in the industry automation system to securely authenticate a remote device, to build up a secured connection, and exchange data in a protected way.
Proper hardware anchors are security-certified components that are also equipped with measures to protect them against physical attacks. As such, they offer protection during transit. In other words, a hardware anchor protection is so robust that it does not need special security measures to be shipped using cost-efficient logistics channels. This not only applies to shipping the security chip itself but, more importantly, also to shipping devices that contain a hardware anchor with customer-specific keys. These physical protection capabilities can reduce costs particularly during installation and delivery processes.
Examples of hardware-based security implementations in smart factories
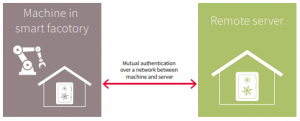
Mutual authentication (figure 2) refers to two parties authenticating (securely identifying) each other. In the context of smart factories, this could be a server and a machine authenticating each other before initiating a secured communication or a critical remote maintenance task such as adaptation of critical parameters. In this scenario, the secured identity stored in the machine’s hardware anchor is verified by the server and vice-versa. The hardware anchor contains the secret keys and offers functionalities to verify the secured identities of the other parties. It usually does this using a public key infrastructure (PKI) scheme.
When an industrial automation system is set up, the computing and controlling components are equipped with a specific version of the relevant software package. After this point in time, the smart factory must be protected against unintended changes to the software as this could disrupt production, threaten plant safety and enable know-how to be stolen. At the same time, it must still be possible for software to be updated intentionally, for example, for maintenance purposes or to change certain features. Robust trust anchors also support this use case, for example by enabling a secured boot process (figure 3). The underlying concept here is that code is only executed after its integrity has been verified in advance by the hardware anchor.
By using state-of-the-art microcontrollers and stand-alone security controllers such as the OPTIGA product family (figure 4), it is possible to implement a hardware-based trust anchor that protects the system software against attacks. The key to successful protection lies in the use of open industry standards that allow seamless connectivity across existing and new systems.
Scalable and dedicated security solutions
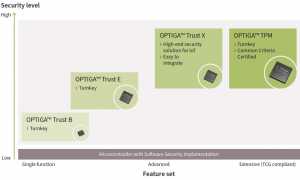
For many manufacturers, protecting their products against counterfeit is a top priority. With its OPTIGA Trust product family, Infineon offers a complete security solution comprising a chip and software for electronic accessories. The chip is based on asymmetric cryptography and is easily integrated into electronic accessories thanks to its compact package (2 mm x 3 mm) and turnkey set-up. In order to check whether or not a part is genuine,the host systems ends a challenge (essentially a random number) to the chip in the accessory. The OPTIGA Trust B subsequently generates a response using the chip-individual key. If successfully authenticated by the chip, the accessory or replacement part is accepted by the system and can be used without restrictions.
Following the same principle, the OPTIGA Trust E was specifically developed for protection of high-value goods in industrial applications. It features an I2C interface as well as an extended temperature range (-40 to +85 °C). This would be of benefit to manufacturers of wind turbines, for example, who would want to avoid damage to the overall system caused by counterfeit replacement parts. Both the OPTIGA Trust B and the OPTIGA Trust E are delivered with code to simplify integration of the chip into spare parts.
The OPTIGA Trust X completes the portfolio of turn-key solutions. Based on a Common Criteria EAL6+ certified hardware, this security solutions enables frequently required security use cases including support for secured communication via (D)TLS, secured firmware update. Furthermore OPTIGA Trust X provides a powerful cryptographic toolbox to efficiently support the growing number of Iot security specifications and protocols.
Comprehensive protection with Trusted Platform Modules (TPMs)
The OPTIGA TPM (Trusted Platform Module) portfolio covers the broadest range of security requirements. These security controllers are based on the international standard of the Trusted Computing Group, an association of leading manufacturers from the IT industry. TPMs have already successfully proven themselves in computer applications, and this technology is now making its way into new networked systems and devices such as routers, industrial facilities and cars.
The members of the OPTIGA TPM family (figure 5) have been validated and security-certified according to the Common Criteria certification process. To permit easy integration into a system, the OPTIGA TPM family supports commercial and open source code for Windows and Linux, including derivatives and Infineon tools. The OPTIGA TPM family comprises a broad range of security controllers complying with the TPM 2.0 standard, which, depending on the application area, are available for various temperature ranges and offer different interfaces such as SPI, I2C and LPC.

One area where OPTIGA TPMscan be used in industrial applications is secured data transmission or storage. In such an application, the key factor is the combination of secured hardware and software-based security mechanisms. The use of a TPM supports monitoring and/or protection of the system’s integrity. This security controller additionally permits reliable component identification, which only allows reliable and trustworthy components to communicate with each other.
For secured remote access, e.g. for system maintenance or software updates, the TPM controls access to the system by means of device authentication. The OPTIGA TPM also provides secured storage for secret keys and protects cryptographic operations. For typical applications such as for the SSL/TLS protocol, keys are stored in the secured store of the TPM rather than in the memory of the main processor and are only processed internally. This offers the advantage that the secret keys are protected against external security risks. In conjunction with TPM and security mechanisms such as encryption, the system code is also protected against manipulation. As a standardized component, TPMs come with a rich ecosystem of available drivers and software stacks allowing customers to easily integrate security with limited integration effort.
Summary
Security is a cornerstone of Industry 4.0. Securedcryptographic identification of machines and devices protects smart factories against manipulation and data theft. Hardware trust anchors implemented with dedicated security chips provide robust protection for security keys while lowering overall security expenses for device manufacturers.