Introduction
Nowhere else is the shift toward digitization as noticeable as in the industrial sector. The production landscape keeps changing—it is networked, and there is increasing communication among different company divisions or even across company boundaries. There is a lively exchange of countless, diverse data between all parties involved in a company, whether human or machine. Where previously only individual machines were connected to each other, in the future networking will be omnipresent—from individual sensors and actuators to machines and complete systems.
All production participants are connected thanks to the transition to digitization driven by Industry 4.0 or the Industrial Internet of Things (IIoT). Ethernet and industrial Ethernet are increasingly emerging as essential communication standards since they provide decisive advantages over previous field buses such as greater transmission rates and higher reliability. In addition, industrial Ethernet offers the possibility to bring the entire communications technology within a network (from the sensor to the cloud) to one unique standard. It complements the classical Ethernet with real-time functions and determinism.
We speak of time sensitive networking (TSN), an association of several sub-standards that are being developed within the framework of the standardization group IEEE 802 (Time Sensitive Networking Task Group) and that define mechanisms for data transmission with the lowest possible latency or high availability. The basis of these TSN networks, however, are innumerable sensors, devices, and systems that are increasingly being equipped with artificial intelligence and will be able to make their own decisions in the future. Such autonomous systems and the resulting increase in the volume of data present manufacturers of automation systems, especially in the field of IT and cyber security, with extreme challenges.
In the future, well-isolated machine areas will have to be open and accessible for communication to the outside world. Demand for cyber security is becoming increasingly important in comparison to pure process reliability or production availability, with a strong dependence of these areas on one another. This is not the only reason for the increased awareness of cyber security. Even recent incidents such as Stuxnet, Wanna Cry, or the attack on the German Bundestag are an enormous boost to the importance of cyber security.
Cyber security, however, is a complex matter due to the protection objectives for confidentiality, integrity, and availability. Confidentiality is possible only when unauthorized information retrieval is not possible. Integrity includes both the correctness of the data (data integrity) and the correct functioning of the system (system integrity). Availability refers to the degree of functionality of the information technology systems; that is, whether the systems are ready for use at any time and whether the data processing also runs correctly. Further protection goals such as authentication and authorization clarify the identity of the user and their access rights to the secure source of the data. Commitment/non-repudiation ensures that the communication participants do not reject messages.
Cyber security therefore deals with a constantly changing problem, which is an issue throughout the life cycle of devices, systems, and networks. As new vulnerabilities are constantly uncovered and new methods of hacking found, it is necessary to update the devices and systems again and again and eliminate the identified vulnerabilities. Systems must therefore be designed to allow for secure updates to important functions and thus be permanently protected. However, this is very difficult for automakers and developers of such systems to implement ever-changing security requirements in their applications, as this is a very broad subject area and thus goes beyond the scope of their actual work. It therefore makes sense to work together with appropriate IT and security experts at an early stage of development. Otherwise, there is a risk that undetected vulnerabilities could potentially damage businesses that are far in excess of the potential benefits of the new products and technologies, or at worst may even endanger their business.
Traditionally, cyber security was seen as an IT issue that required the implementation of secure operating systems, network and application protocols, firewalls, and other network-intrusion prevention solutions. However, as a result of the transition to digitalization, machines will have to be as intelligent and autonomous as possible in the future, resulting in more functionality, more connectivity, and, at the same time, higher data volumes. As a result, there is a significant increase in the importance of system risk assessment. Where previously some systems did not require safety or protection, they are now critically vulnerable to attacks that can leave them paralyzed. For the manufacturers of such promising systems, it is important to carefully check and evaluate potential vulnerabilities and to take appropriate protective measures.
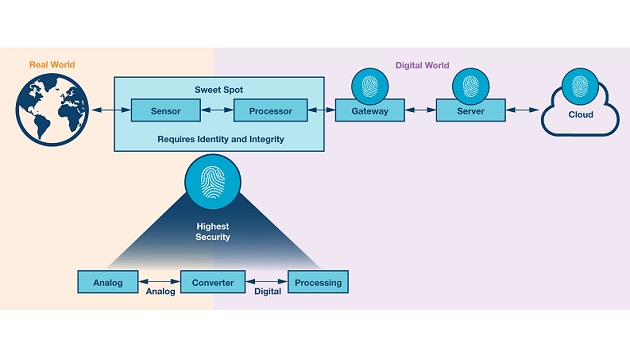
The implementation of appropriate security functions should happen as early as possible, preferably right at the beginning of the system signal chain; that is, at the transition from the real, physical world to the digital world. This period is the so-called sweet spot, and it seems to be the most promising point of the signal chain. This point is usually formed by the sensor or actuator. Here, the complexity of coding the trusted data is usually relatively low, which can also increase confidence in data-based decisions. However, as shown in Figure 1, this sweet spot requires a high degree of hardware identity and data integrity in order to achieve the highest level of data security and thus the confidence of the operating systems in secure data. The implementation of identities and integrity already at the hardware level—that is, protective features already embedded in silicon— offer the most promising approach for generating appropriate data security. This is where the so-called root of trust begins.
Root of Trust
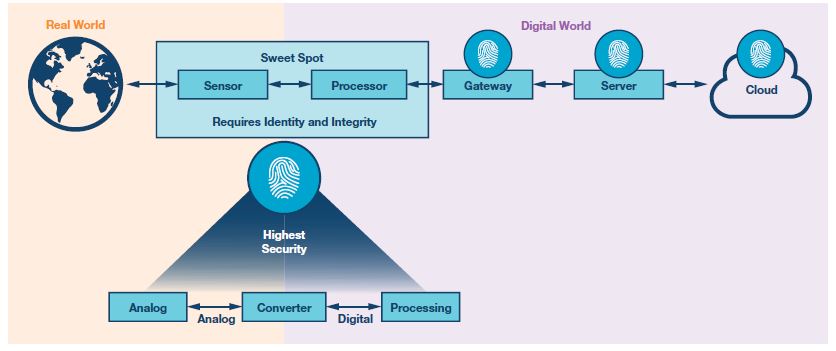
The root of trust is a set of related security functions that control the cryptographic process in the devices as a largely separate computing unit. In this case, a secure data transmission is usually generated by controlling hardware and software components in sequentially linked steps. The sequence of the individual steps, as shown in Figure 2, ensures that the data communication proceeds as desired and unharmed. As a result, a well-protected application can be assumed.
Securing a trustworthy, nonvulnerable application is done first by using your own identity or your own key. Here the access authorizations of the devices or persons are assigned and checked. Although identities and keys are established, they are still the most critical element in this first step of the root of trust, because the device is only as secure as the protection of the key. For this reason, it is necessary to implement additional protection functions, which ensure secure storage of the key and forwarding to the right recipient.
In order to be able to protect the actual functions of the devices from unauthorized access, a secure boot process is required when the devices are started. Authentication and subsequent deciphering of the software will ensure that the devices are protected from attack and manipulations. Without a secure boot, it is relatively easy for potential attackers to intrude, manipulate, and execute error-prone codes.
Secure updates are an important step in handling the ever-changing application environment and emerging security vulnerabilities. As soon as new hardware or software vulnerabilities are discovered, they should be remedied as soon as possible by updating the devices, even before major damage can be caused by attacks. Secure updates are also performed to fix any product errors or to implement product improvements.
In order for a trusted environment to perform additional security services, such as cryptographic application programming interfaces (APIs), are required. It also includes protection features such as encryption, authentication, and integrity.
All of these security functions should be placed in a separate and protected execution environment from the actual applications of the equipment to ensure that there are no errors in the codes that could result in consequential damage to the equipment.
Cyber Security, a Growing Issue for Semiconductor Manufacturers
Semiconductor manufacturers such as Analog Devices, Inc. (ADI), one of the leading suppliers of future proof products for the mega trends of IIoT and Industry 4.0, have been concerned with cyber security for quite some time. To meet the increasing security requirements, Analog Devices tries to incorporate the concept of the root of trust in its products and developments. The goal is to be able to offer appropriate attack-resistant products for those areas or industries for which they are of concern, thus ensuring the highest degree of customer confidence and a significant increase in the value of their applications. This means, primarily, to introduce security where there is a connection to a network. This mainly refers to semiconductor products for the communications sector, especially industrial Ethernet and TSN components. Furthermore, security is also inevitable wherever an integrated system is present on a chip; that is, where a microprocessor handles essential functionality.
A decisive factor for manufacturers is early cooperation with customers who may already be in the definition phase of their projects. This allows the most basic security requirements to be included in the designs, protecting the entire signal chain. Thus, identities can already be embedded on the physical level, directly at the sensor node of the signal chain, which ensures greater confidence in the security of the data communication. It is for this reason, among others, why Analog Devices has expanded its cyber security expertise and acquired Sypris Electronics’ Cyber Security Solutions (CSS) division.
Thanks to this acquisition, a renowned manufacturer of highly secure technologies for cyber security and provider of security services has been created, which will enable Analog Devices to offer its customers highly flexible, reliable, and integrated system-level security solutions in the future. With secure key generation/management, secure booting, secure updates, secure memory access, and secure debugging, these so-called CSS security solutions extend beyond traditional encryption technologies. They offer a fully integrated replacement for classic cryptographic solutions and in the future will enable the realization of highly secure hardware platforms without much effort, leading to a significant increase in the value of the products they offer customers.
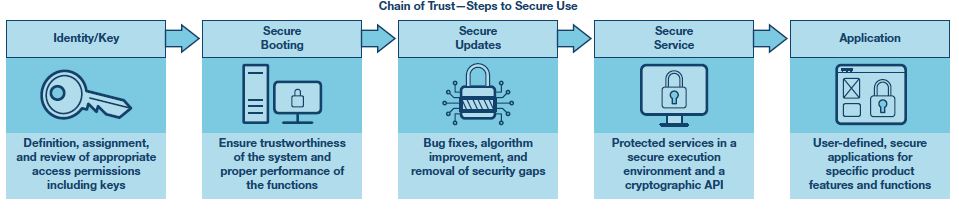
CSS cyber security technology, or rather all its security functions, is usually implemented on a separate FPGA-based subsystem that runs parallel to the actual application functions of the chip. This is called a trusted execution environment (TEE), as shown in Figure 3.
The FPGA-based implementation easily enables software upgrades of field devices, eliminating any potential product vulnerabilities with little effort.
Unlike software-based encryption technologies, this hardware-based solution uses a dedicated processor to calculate encryption algorithms and dedicated storage for secure key hosting. The dedicated memory is only accessible via the dedicated processor. By using the dedicated components, the TEE and all sensitive operations can be isolated from the rest of the system, increasing the speed of execution of the encryption functions while significantly reducing the potential attack surface for hackers.
It prevents any unauthorized access to the rest of the chip, while access to the cryptographic functionality takes place via the API interface. As a result, a very high degree of security can be achieved.
Conclusion
Cyber security and the protection of technical systems from possible attacks are key elements in the transition to digitization, especially in the automation industry. Due to a lack of regulations and, above all, a lack of knowledge in cyber security, many companies still have great uncertainty as to how to tackle this important issue.
The evaluation of (acceptable) risks to their processes is only the beginning, but a central point. But how can cyber security be further anchored in companies and their products? Above all, manufacturing companies depend on the support of experts and their know-how.
Analog Devices has been addressing this issue for quite some time and has set itself the task of developing a secure portfolio that facilitates the introduction of security solutions and builds trust in order to push ahead with the introduction of Industry 4.0 and IIoT.
These include developments of turnkey, hardware-based solutions that allow customers to easily integrate data security into their products. With many advantages over software-based encryption technologies, semiconductor manufacturers are increasingly focusing on hardware-based cryptographic solutions to support cutting-edge technology solutions and protect them from unwanted attacks. Most sensitive applications, where security and reliability are critical, such as in the industrial automation, automotive, energy, and critical infrastructure markets, can be offered the highest level of security.