Organizations are losing the cyber security race. Cyber threats are evolving faster than security teams can adapt. The proliferation of data from dozens of security products are outpacing the ability for security teams to process it. And budget and talent shortfalls limit the ability for security teams to expand rapidly.
The question is how does a network security team improve the ability to scale and minimize data breaches, all the while dealing with increasingly complex attack vectors? The answer is automation.
Automation & Security
Four in five organizations reported facing some form of network- or application-based cyber attack in 2017, according to Radware’s 2017-2018 Global Application & Network Security Report. Zero-day malware, botnets and Burst attacks – all sterling examples of automated attack vectors – saw significant increases in usage in 2017, according to the same report.
The numbers don’t lie. Cyber criminals are becoming savvier and their attacks increasingly automated. Furthermore, it’s evident that traditional DDoS mitigation methods, such as rate-based or manually-tuned protection, are outdated solutions to safeguard sensitive data in the wake of automated cyber attacks.
IT organizations now face advanced persistent threats that are spearheaded not by human assailants, but by automated bots. Security personnel are no match for these intense, sustained attacks and are incapable of keeping up with the sheer volume of incoming threats. Legacy DDoS mitigation solutions that leverage rule-based event correlation can generate thousands of alerts in a 24-hour span. On a good day, an SOC can only investigate approximately a hundred.
Additionally, their ability to make quick and impactful decisions to manually address an attack is equally inefficient. Research shows that machine-learning botnets are now capable, in certain situations, of scanning a network for vulnerabilities and successfully breaching its defenses in less than 20 seconds.This is why automation is becoming such a powerful and effective component of cyber security. To combat the onslaught of incoming threats, organizations must employ an army of equivalent strength and sophistication.
How Attackers Leverage Automation
Cyber criminals are weaponizing automation and machine learning to create increasingly evasive attack vectors, and the Internet of Things (IoT) has proven to be the catalyst driving this trend. IoT is the birthplace for many of the new types of automated bots and malware.
At the forefront are botnets, which are increasingly sophisticated, lethal and highly automated digitized armies running amok over corporate networks. For example, hackers now leverage botnets to conduct early exploitation and network reconnaissance prior to unleashing an attack.The Mirai botnet, which was made famous by its use in the 2016 attack on DNS provider Dyn, and its subsequent variants, embodies many of these characteristics. It leverages the infamous Water Torture attack to generate randomized domain names on a DNS infrastructure. Follow up variants use automation to allow the malware to craft malicious queries in real-time.
Modern day malware is an equally sophisticated multi-vector cyber attack weapon designed to elude detection using an array of evasion tools and camouflage techniques. Hackers now leverage machine learning to create custom malware that defeats anti-malware defenses. One example is Generative Adversarial Network algorithms that can bypass black-box machine learning models. In another example, a cyber security company adapted Elon Musk’s Open AI framework to create forms of malware that mitigation solutions couldn’t detect.
Automation for Detection and Mitigation
So how does a network security team improve its ability to deal with these increasingly multifarious cyber attacks? Fight fire with fire. Automated cyber security solutions provide the data-processing muscle to mitigate these advanced threats.
Executives clearly understand this and are ready to take advantage of automation. According to Radware’s C-Suite Perspectives: Trends in the Cyber attack Landscape, Security Threats and Business Impacts, the vast majority of executives (71%) report shifting more of their network security budget into technologies that employ machine learning and automation. The need to protect increasingly heterogeneous infrastructures, a shortage in cyber security talent and increasingly dangerous cyber threats were indicated as the primary drivers for this fiscal shift.In addition, the trust factor is increasing. Four in 10 executives trust automated systems more than humans to protect their organization against cyber attacks, according to the same report.
Traditional DDoS solutions use rate limiting and manual signature creation to mitigate attacks. Rate limiting can be effective but can also result in a high number of false positives. As a result, manual signatures are then used to block offending traffic to reduce the number of false positives. Moreover, manual signatures take time to create because identifying offending traffic is only possible AFTER the attack starts. With machine-learning botnets now breaching defenses in less than 20 seconds, this hands-on strategy does not suffice.
Automation, and more specifically machine learning, overcomes the drawbacks of manual signature creation and rate-limiting protection by automatically creating signatures and adapting protections to changing attack vectors. Machine learning leverages advanced mathematical models and algorithms to look at baseline network parameters, assess network behavior, automatically create attack signatures and adapt security configurations and/or policies to mitigate attacks. Machine learning transitions an organization’s DDoS protection strategy from manual, ratio- and rate-based protection to behavioral-based detection and mitigation (see Figure 1).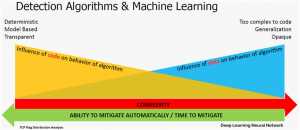
Automation is the future of cyber security. As cyber criminals become savvier and increasingly rely on automation to achieve their mischievous goals, automation and machine learning will become the cornerstone of cyber security solutions to effectively combat the onslaught from the next generation of attacks. It will allow organizations to improve the ability to scale network security teams, minimize human errors and safeguard digital assets to ensure brand reputation and the customer experience.









